5G networks and network slicing
Management and orchestration of 5G networks and network slicing is a feature that includes the following work items: management concept and architecture, provisioning, network resource model, fault supervision, assurance and performance management, trace management and virtualization management aspects. With the output of these work items, SA5 provides specified management interfaces in support of 5G networks and network slicing. An operator can configure and manage the mobile network to support various types of services enabled by 5G, for example eMBB (enhanced Mobile Broadband) and URLLC (Ultra-Reliable and Low Latency Communications), depending on the different customers’ needs. The management concept, architecture and provisioning are being defined in TS
28.530,
28.531,
28.532 and
28.533.
Network slicing is seen as one of the key features for 5G, allowing vertical industries to take advantage of 5G networks and services. 3GPP SA5 adopts the network slice concept as defined in SA2 and addresses the management aspects. Network slicing is about transforming a PLMN from a single network to a network where logical partitions are created, with appropriate network isolation, resources, optimized topology and specific configuration to serve various service requirements.
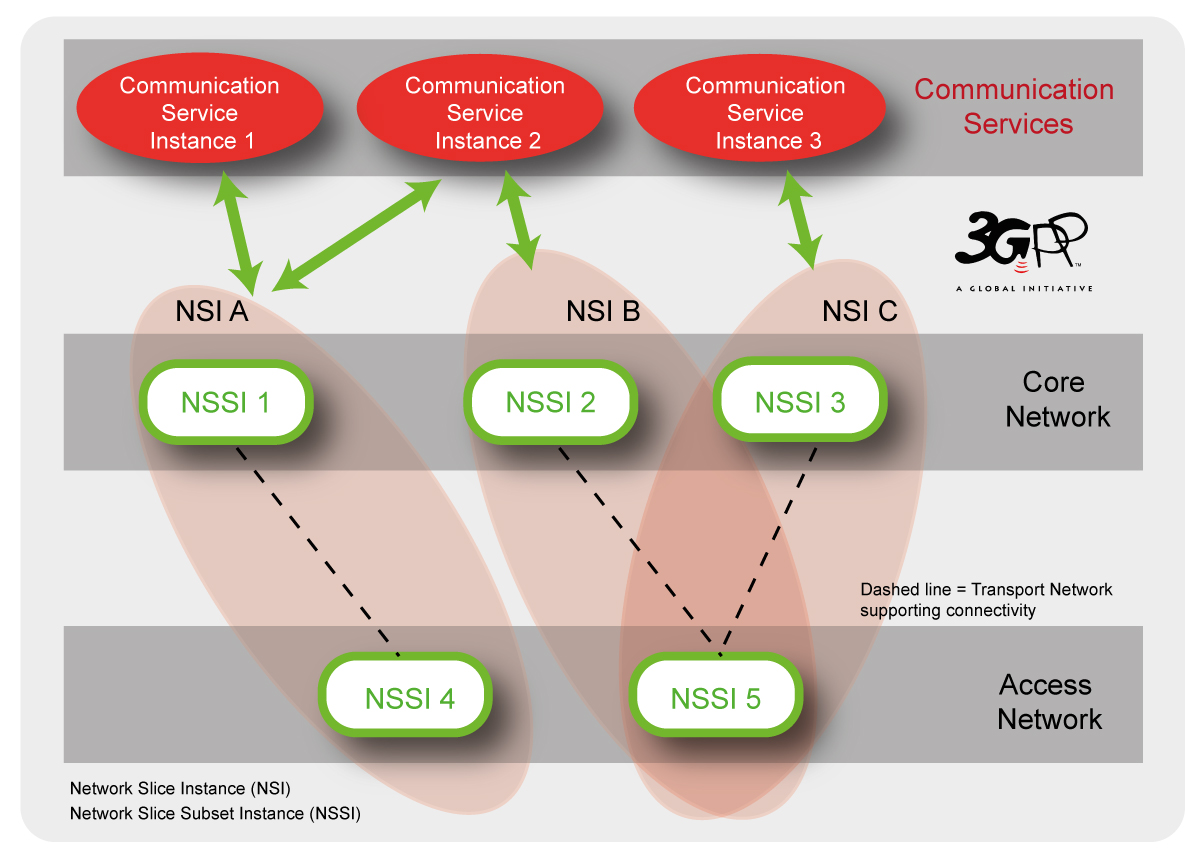
As an example, a variety of communication service instances provided by multiple Network Slice Instances (NSIs) are illustrated in the figure below. The different parts of an NSI are grouped as Network Slice Subnets (e.g. RAN, 5GC and Transport) allowing the lifecycle of a Network Slice Subnet Instance (NSSI) to be managed independently from the lifecycle of an NSI.
Provisioning of network slice instances
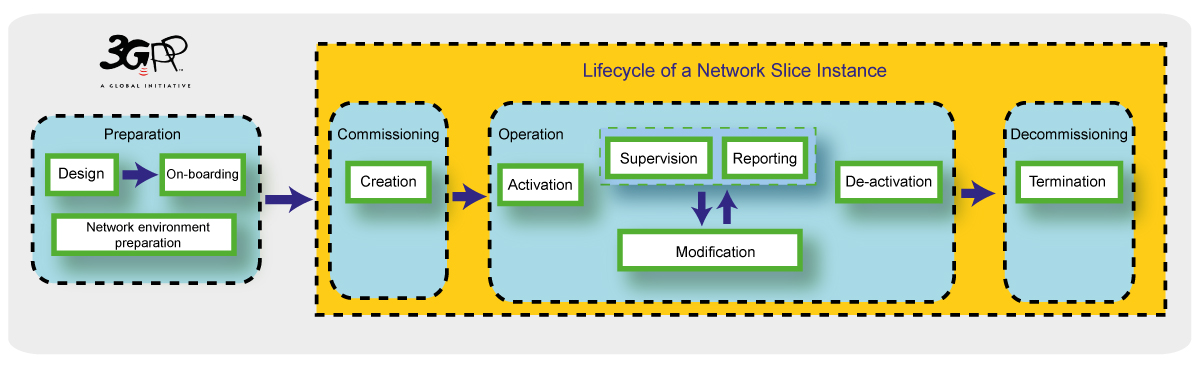
The management aspects of a network slice instance can be described by the four phases:
1) Preparation: in the preparation phase the network slice instance does not exist. The preparation phase includes network slice template design, network slice capacity planning, on-boarding and evaluation of the network slice requirements, preparing the network environment and other necessary preparations required to be done before the creation of a network slice instance.
2) Commissioning: provisioning in the commissioning phase includes creation of the network slice instance. During network slice instance creation all needed resources are allocated and configured to satisfy the network slice requirements. The creation of a network slice instance can include creation and/or modification of the network slice instance constituents.
3) Operation: includes the activation, supervision, performance reporting (e.g. for KPI monitoring), resource capacity planning, modification, and de-activation of a network slice instance. Provisioning in the operation phase involves activation, modification and de-activation of a network slice instance.
4) Decommissioning: network slice instance provisioning in the decommissioning phase includes decommissioning of non-shared constituents if required and removing the network slice instance specific configuration from the shared constituents. After the decommissioning phase, the network slice instance is terminated and does not exist anymore.
Similarly, provisioning for a network slice subnet instance (NSSI) includes the following operations:
- Create an NSSI;
- Activate an NSSI;
- De-active an NSSI;
- Modify an NSSI;
- Terminate an NSSI.
Roles related to 5G networks and network slicing
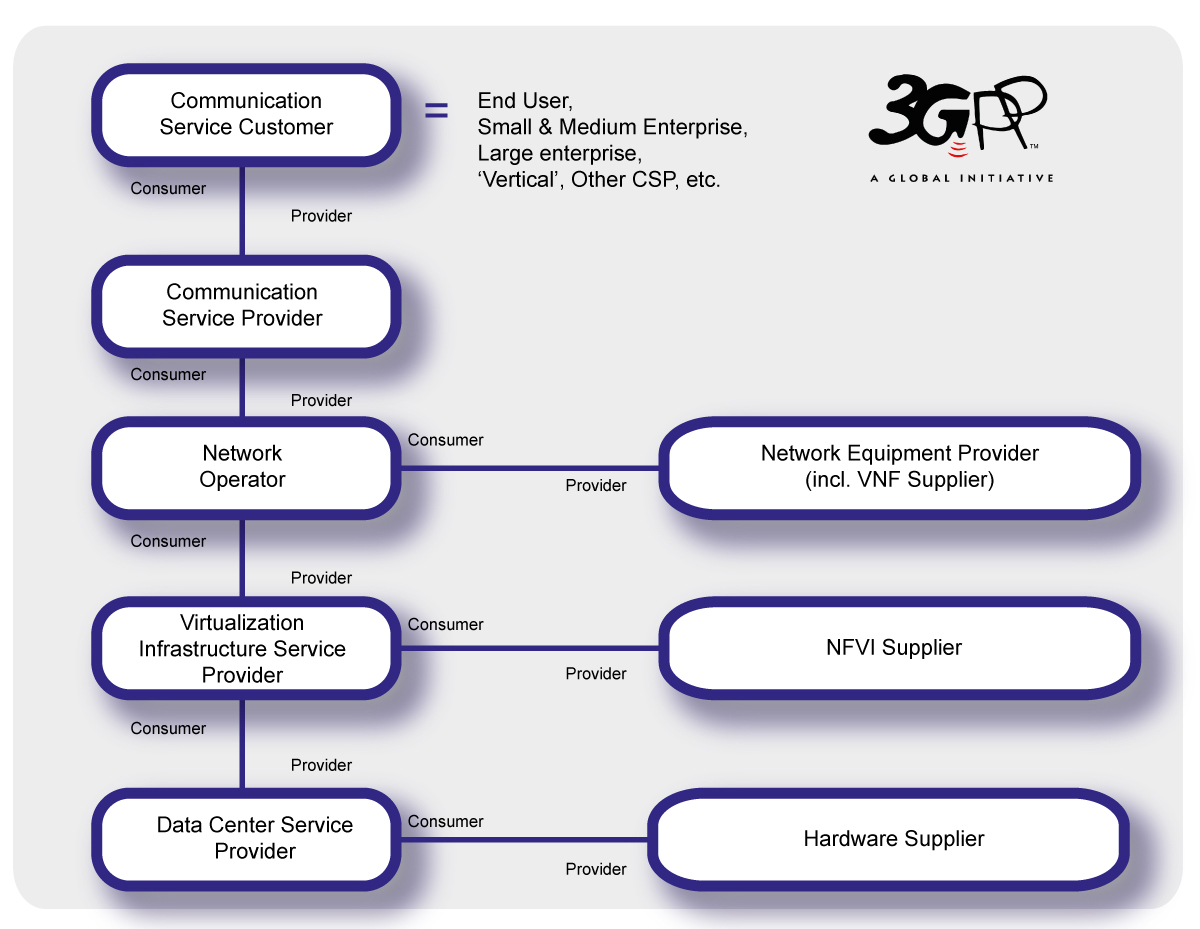
The roles related to 5G networks and network slicing management include: Communication Service Customer, Communication Service Provider (CSP), Network Operator (NOP), Network Equipment Provider (NEP), Virtualization Infrastructure Service Provider (VISP), Data Centre Service Provider (DCSP), NFVI (Network Functions Virtualization Infrastructure) Supplier and Hardware Supplier.
Depending on actual scenarios:
- Each role can be played by one or more organizations simultaneously;
- An organization can play one or several roles simultaneously (for example, a company can play CSP and NOP roles simultaneously).
Management models for network slicing
Different management models can be used in the context of network slicing.
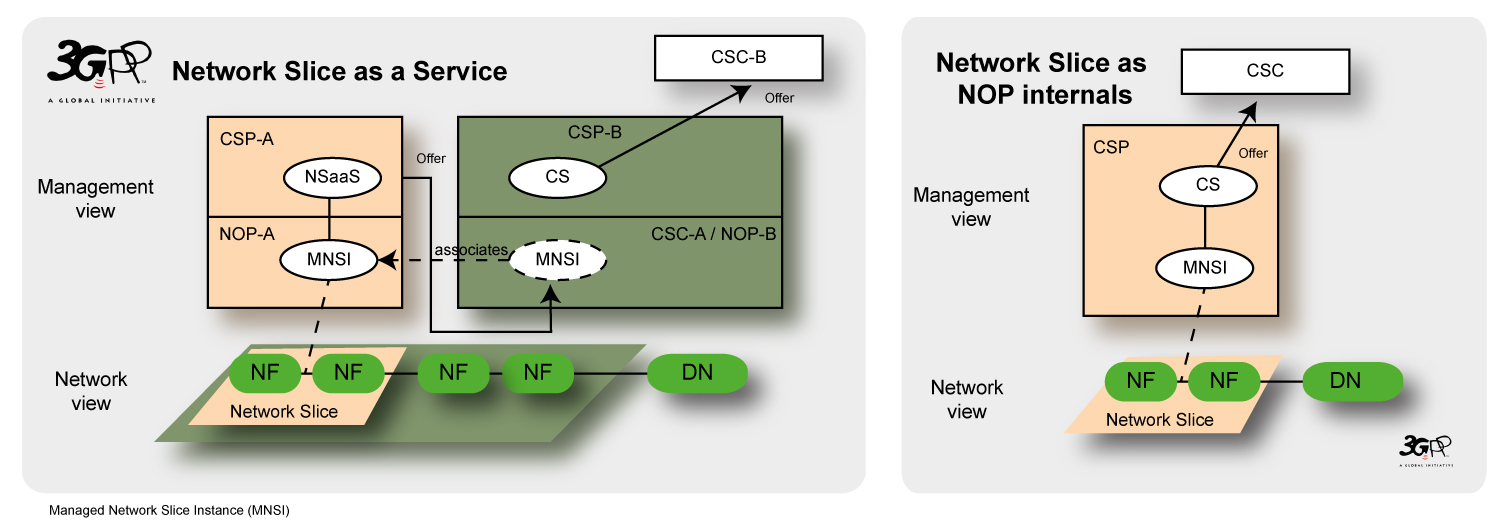
1) Network Slice as a Service (NSaaS): NSaaS can be offered by a CSP to its CSC in the form of a communication service. This service allows CSC to use and optionally manage the network slice instance. In turn, this CSC can play the role of CSP and offer their own services (e.g. communication services) on top of the network slice instance. The MNSI (Managed Network Slice Instance) in the figure represents a network slice instance and CS represents a communication service.
2) Network Slices as NOP internals: network slices are not part of the CSP service offering and hence are not visible to CSCs. However, the NOP, to provide support to communication services, may decide to deploy network slices, e.g. for internal network optimization purposes.
Management architecture
SA5 recognizes the need for automation of management by introducing new management functions such as a communication service management function (CSMF), network slice management function (NSMF) and a network slice subnet management function (NSSMF) to provide an appropriate abstraction level for automation.
The 3GPP SA5 management architecture will adopt a service-oriented management architecture which is described as interaction between management service consumer and management service provider. For example, a management service consumer can request operations from management service providers on fault supervision service, performance management service, provisioning service and notification service, etc.
Network Resource Model (NRM) for 5G networks and network slicing
To support management and orchestration of 5G networks, the Network Resource Model (NRM) representing the manageable aspects of 5G networks needs to be defined, according to 5G network specifications from other 3GPP working groups as well as considering requirements from 5G management architecture and operations.
The 5G NRM specifications family includes 4 specifications: TS
28.540 and TS
28.541 for NRM of NR and NG-RAN, TS
28.542and TS
28.543 for NRM of 5G core network.
According to content categorization, 5G NRM specifications can be divided into 3 parts:
- Requirements, also known as stage 1,
- Information Model definitions also known as stage 2, and
- Solution Set definitions also known as stage 3.
Identified in the specifications of 5G NRM requirements (TS
28.540 and TS
28.542), the NRM of 5G network comprises NRM for the 5G core network (5GC) and NRM for 5G radio access network (i.e. NR and NG-RAN). The 5GC NRM definitions support management of 5GC Network Functions, respective interfaces as well as AMF Set and AMF Region. The NR and NG-RAN NRM definitions cover various 5G radio networks connectivity options (standalone and non-standalone radio node deployment options) and architectural options (NR nodes with or without functional split).
The 5G Information Model definitions specify the semantics and behavior of information object class attributes and relations visible on the 5G management interfaces, in a protocol and technology neutral way (UML as protocol-neutral language is used). The 5G Information Model is defined according to 5GC, NR and NG-RAN specifications. For example, in 3GPP TS
38.401, the NR node (gNB) is defined to support three functional split options (i.e. non-split option, two split option with CU and DU, three split option with CU-CP, CU-UP and DU), so in the NR NRM Information Model, corresponding Information Object Class (IOC) is defined for each network function of gNB specified, and different UML diagrams show the relationship of each gNB split option respectively. Further, in the 5G Information Model definitions, the existing Generic NRM Information Service specification (TS
28.622) is referenced to inherit the attributes of generic information object classes, and the existing EPC NRM Information Service specification (TS
28.708) is referenced for 5GS / EPS interworking relationships description.
Finally, NRM Solution Set definitions map the Information Model definitions to a specific protocol definition used for implementations. According to recommendation from TR
32.866 (Study on RESTful based Solution Set), JSON is expected to be chosen as data modelling language to describe one 5G NRM Solution Set.
Fault Supervision of 5G networks and network slicing
Fault Supervision is one of the fundamental functions for the management of a 5G network and its communication services. For the fault supervision of 5G networks and network slicing, the following 3GPP TSs are being specified:
1) TS
28.545 “Management and orchestration of networks and network slicing; Fault Supervision (FS); Stage 1”, which includes:
- The use cases and requirements for fault supervision of 5G networks and network slicing.
- The definitions of fault supervision related management services (e.g. NetworkSliceAlarmAcknowledgement, NetworkSliceAlarmListReading, NetworkSliceAlarmClearance, NetworkSliceAlarmNotification, NetworkSliceAlarmSubscription, etc.)
2) TS
28.546 “Management and orchestration of networks and network slicing; Fault Supervision (FS); Stage 2 and stage 3”, which includes the definition of:
- Interfaces of the fault supervision related management services; (Stage 2)
- Notifications; (Stage 2)
- Alarm related information models (e.g. alarmInformation, alarmList, etc.); (Stage 2)
- Solution set(s) (e.g. RESTful HTTP-based solution set for Fault Supervison); (Stage 3)
- New event types and probable causes if necessary.
Assurance data and Performance Management for 5G networks and network slicing
The 5G network is designed to accommodate continuously fast increasing data traffic demand, and in addition, to support new services such as IoT, cloud-based services, industrial control, autonomous driving, mission critical communications, etc. Such services may have their own performance criteria, such as massive connectivity, extreme broadband, ultra-low latency and ultra-high reliability.
The performance data of the 5G networks and NFs (Network Functions) are fundamental for network monitoring, assessment, analysis, optimization and assurance. For the services with ultra-low latency and ultra-high reliability requirements, any faults or performance issues in the networks can cause service failure which may result in serious personal and property losses. Therefore, it is necessary to be able to collect the performance data in real-time (e.g., by performance data streaming), so that the analytic applications (e.g., network optimization, SON, etc.) could use the performance data to detect any network performance problems, predict the potential issues and take appropriate actions quickly or even in advance.
For network slicing, the communication services are provided on top of the end-to-end network slice instances, so the performance needs to be monitored from end-to-end point of view.
The end to end performance data of 5G networks (including sub-networks), NSIs (Network Slice Instances) and NSSIs (Network Slice Subnet Instances) are vital for operators to know whether they can meet the communication service requirement.
The performance data may be used by various kinds of consumers, such as network operator, SON applications, network optimization applications, network analytics applications, performance assurance applications, etc. To facilitate various consumers to get their required performance data, the following items are being pursued by this WI:
- A service based PM framework and a list of PM services as described in the table below:
- Performance measurements (including the data that can be used for performance assurance) for 3GPP NFs;
- End to end KPIs, performance measurements (including the data that can be used for performance assurance) for NSIs, NSSIs and networks (where the performance data is not specific to network slicing).